
Encrypt It Yourself Pt I: The Encrypted Webmail Trap
This new four-part series is aimed to provide you with the tools you need to protect sensitive communications, even when operating on centralized platforms such as an email provider or Telegram.
We will cover different communication modalities and the mechanisms used to protect your information. The first entry in the series takes a look at email and how it works, explaining the difference between encrypted webmail and open standards. It ends with you registering an IMAP/SMTP account and setting it up on your client of choice.
The following parts will guide you through end to end encrypting your own mail and other communications!
Watch The Video
Email is essential to digital communication, no doubt you have one or multiple. Your accounts are associated with almost all the user accounts you have on the internet. They are usually the second point of access if your password fails (Forgot Password). Email is a powerful tool.
With the growth of internet surveillance, and the growth of our privacy-aware movement, we've seen the rise of many privacy focused email providers.
We put immense trust in these providers to keep our emails protected and the content within private. More than trust, we need to have a basic understanding of how email and its encryption works.
Today we will explore the foundations of how Email works, how it can be encrypted, and what to look for when choosing an email service.
At the end, we'll show you how to use open mail protocols like (IMAP/SMTP) along with PGP encryption to encrypt your own mail.
TBOT Challenge
- Get yourself an IMAP/SMTP mail account
(prerequisites for the following videos in the series) - Get yourself a Linux computer
How Email Works
The Protocol
IMAP or Internet Message Access Protocol is the most popular email protocol in use today. It allows for users to connect to a mailbox (mail server) from multiple clients (devices), pulling down emails on demand.
IMAP requires emails to be stored and saved on the server. The earlier POP protocol required emails to be retrieved from the server, but those emails were deleted once pulled down to a device. Because emails are saved on the server, IMAP had the added benefit of allowing multiple devices to connect to the mail server and to be sync. It also allowed users to create folders for their mails, and to search in their mailbox.
How Email Gets Sent
Email is sent using a different protocol, called SMTP or Simple Mail Transfer Protocol.
We write emails in our mail clients (or mail user agents). When we send an email, it is sent from our mail client to a mail server (or message transfer agent), which is responsible for getting it to the intended destination. Usually the path is direct from your mail server to the recipient's mail server, however if the recipient email server is configured to route to additional mail servers, it can pass through additional mail servers before getting to the recipient's inbox.
Email Structure
Every email consists of two main parts, its header (metadata) and its body (or the content).
Header
The header is composed of a set of fields (up to 300) that define some basic information about the email. At a bare minimum, every email should contain the following header fields:
- From (email address, name)
- Date
The To/Subject/CC,Bcc are optional fields that are used commonly. There are more optional fields that help define replies, forwarding, etc.
Body
This is the main content of the email and can be in a simple text (MIME) format or even take the form of a webpage (HTML).
Mail Encryption
What can be Encrypted and Privacy Considerations?
There are two layers of encryption that can be involved when sending email.
First Layer: TLS
Each email must find its way to the recipient mail server through other mail servers and networks. This means that multiple third parties are involved in routing emails to their final destination, and each of these parties could read or store the content. In order to protect the email as its moving between mail servers, TLS encryption can be used.
TLS encryption is a standard on the internet today, and is responsible for encrypting communication between your web browser and the web site you are visiting, preventing any third party from seeing the communication exchange. Although using TLS is widely enforced on the internet (your browser will warn you of insecure sessions), TLS is not enforced when sending email, and there are some email servers that do not support it.
Many email accounts are configured to not enforce TLS, and will attempt to use TLS on each hop, but if a mail server in the chain doesn't not support TLS, the mail would be sent in cleartext. You can configure your email account to enforce TLS (if your server supports its), which will only send the email in an encrypted manner. Its also important to note that each mail server that uses TLS encryption will get receive the email in a decrypted form, which it needs to be able to route it to its final recipient. This is where the second layer of encryption can come in and add more security.
OpenPGP
How does Encryption work?
Here's a basic summary, there's far more to this! Public Key Cryptography like OpenPGP works by using two keys, a public key and a private key. These keys are counterparts to each other. By sharing your public key, your contacts can encrypt a message that can only be decrypted by your private key. Of course, you must never share your private key. Anyone who has your private key can decrypt any and all messages meant for you.
For example:
- Tee is sending an email to their friend, Botto.
- Tee and Botto have shared their public keys with each other in the past.
- Tee encrypts their message with Botto's public key and sends it off to them.
- The message is routed through multiple mail servers until it reaches Botto.
- Botto decrypts the message using their private key (local to their device) automatically.
When we encrypt our mail, we must realize that we can only encrypt the body and not the header fields, since the header fields are needed for the mail to be properly routed. That means the To, From, subject, and other fields will be visible by other mailservers.
How To Encrypt Email On Our Devices
We can encrypt our mail using software that implements the OpenPGP standard, an open standard derived from the original PGP encryption software.
This OpenPGP standard is used widely across different operating systems, implemented in specific applications. We will use OpenPGP to set up our encrypted webmail in the following videos.
How Does Encrypted Webmail Work
Encrypted webmail combines a mail server together with a public key server. Instead of managing your own private keys, a private key is generated for you when your mail account is created. This private key is then saved by your provider, although typically the private key is encrypted with a hash derived from your account password. Your provider has access to this encrypted private key at all times.
Web based encryption is powered by libraries like OpenPGP.js, which ProtonMail and other encrypted mail providers use.
Although this is quite convienient as setting up encrypted webmail is easy as signing into the encrypted webmail app on any device, there's one major concern.
The Encrypted Webmail Trap
In the browser, you can never be certain that the website you are seeing matches up with the repository (code) of the project.
For this reason, if your webmail provider turns malicious or is compromised, they could potentially serve you a website that retrieves your password and/or your private keys.
Encrypted webmail providers already keep your private keys on their servers. Every time you login, you potentially pass over the last piece of the puzzle in the form of your account password. All it takes is one account login that collects your password, and all of your emails in the past and in the future (for that key) are compromised.
This is the major drawback to encrypted webmail, and the reason why ProtonMail was declared not End-To-End encrypted according to security researcher Nadim Kobeissi. Its important to note that this flaw comes from the unverifiable builds of the web application, there is assurance when it comes to mobile applications.
When I was building a prototype for a Above Market - web-based crypto-commerce market, I saw the danger in the above. I opted to offer a way for users to encrypt/decrypt off of the website, where they managed their private keys and there was no possibility of the server storing them.
Trust No One
With this in mind, it makes far more sense to manage your own private keys rather put them in the hands of someone else. Many protocols such as XMPP already provide a system to manage private keys per device in a seamless fashion, which allows for end to end encrypted messaging synced up across all devices. Although XMPP might be a more secure communication method, we are still waiting for its use to catch on.
Encrypt It Yourself
The next video in the series will work through how to encrypt your own mail on desktop & mobile using OpenPGP and an app called OpenKeychain. This way you do not need to trust any third parties to manage your private keys.
Considerations
Due to the way email is routed, the mail header such as the from/to subject, cc/bcc will be public to other mail servers as it is routed through the network.
If you are doing sensitive things, encrypting the body may not be enough. Investigations will often use email metadata to establish that communication occured between two parties in a certain time frame. This information can be requested in the form of a warrant from either email provider. If you want more safety - use another modality like XMPP where warrants are much rarer and messages only pass between two federated servers.
Getting a Mail Account
First thing we need is an IMAP/SMTP mail service. Here are some IMAP/SMTP providers. Your current email provider may also offer IMAP/SMTP, search to see if its available.
- Above Privacy Suite (our service)
- Disroot (free community service)
- Riseup (free community service)
Setup Mail on Desktop & Mobile
Next we want to authenticate and setup our email accounts on our phone and our computer.
Desktop
We are assuming you use a Linux machine, if you don't have one - please check out our Installing Linux article. For desktop we recommend the Evolution mail client. If you are using Windows or macOS you can install Thunderbird.
Here's how you install Evolution from the command line on Ubuntu based machines.
sudo apt install evolution
Mobile
For mobile we are assuming you use a Android phone.
We do not have a recommendation for an iOS app, however there are paid/proprietary clients available. Do your own research here.
You should install the K9-Mail app from F-Droid.
Setup Your Accounts
Next you'll look up your IMAP/SMTP configuration from your email provider, setting up the account on both mail clients.
Your configuration will include:
Username: This is usually your email in full.
Password: The password to your email account.
IMAP Server: The server responsible for receiving mail.
IMAP Port: What port number your server is accepting connections on.
SMTP Server: The server responsible for sending mail.
SMTP Port: What port number your server is accepting connections on.
These are the only configuration items you need to pay attention to.
An example configuration may look like this:
username: takebackourtech@tbot.io
password: mypassword
Incoming Mail: mail.tbot.io
IMAP Port: 993
Outgoing Mail: mail.tbot.io (notice how the incoming/outgoing mail server can be the same)
Outgoing Port: 587
Configuring Evolution
When launching Evolution, you will enter a Welcome page, which will prompt you to add your first mail account.
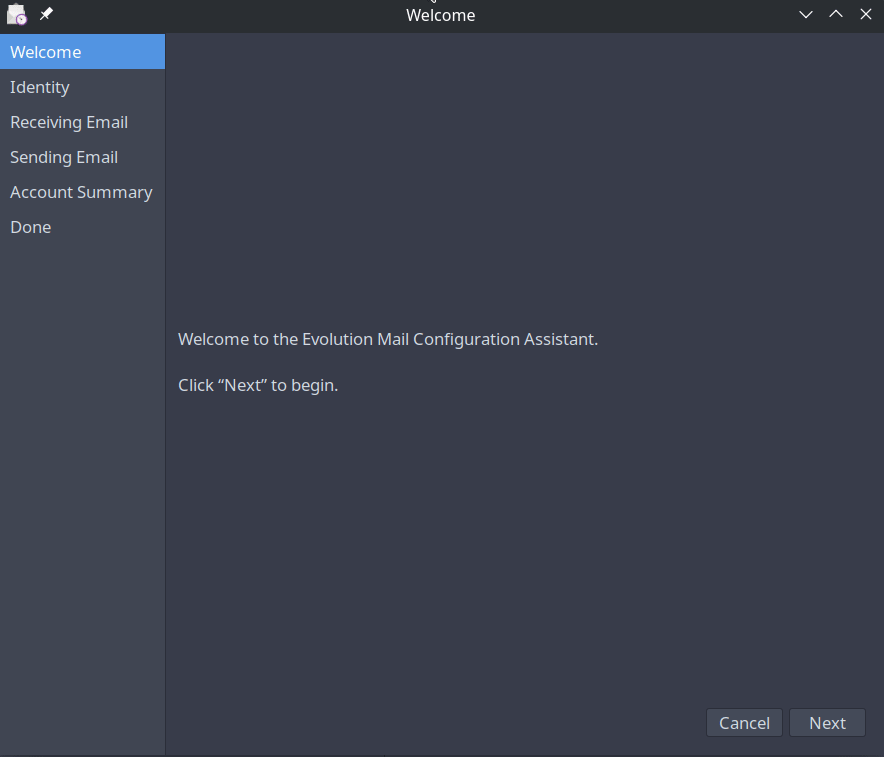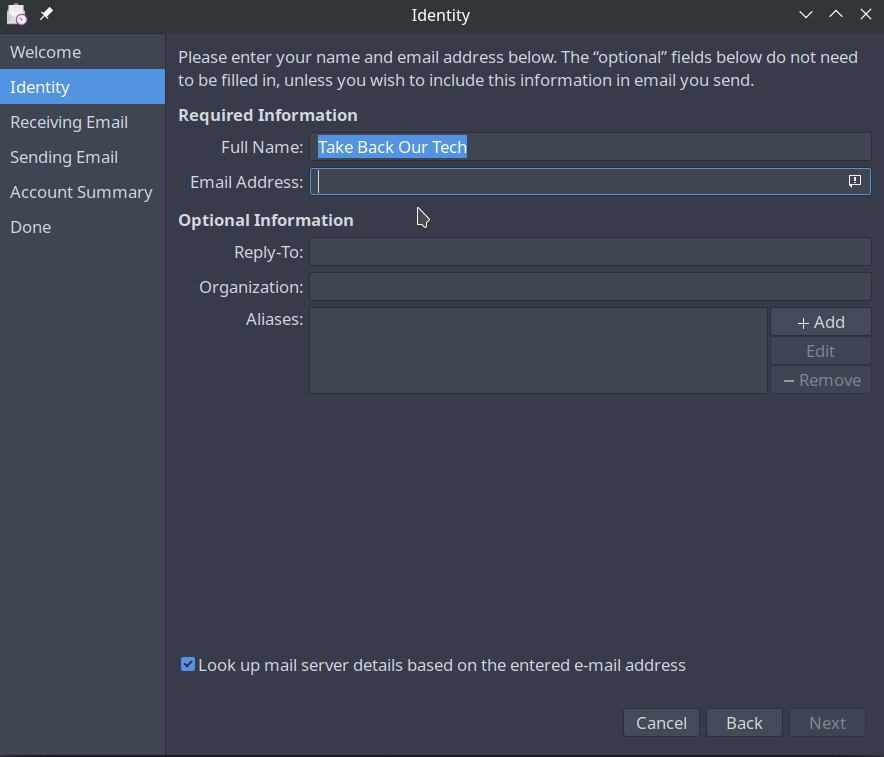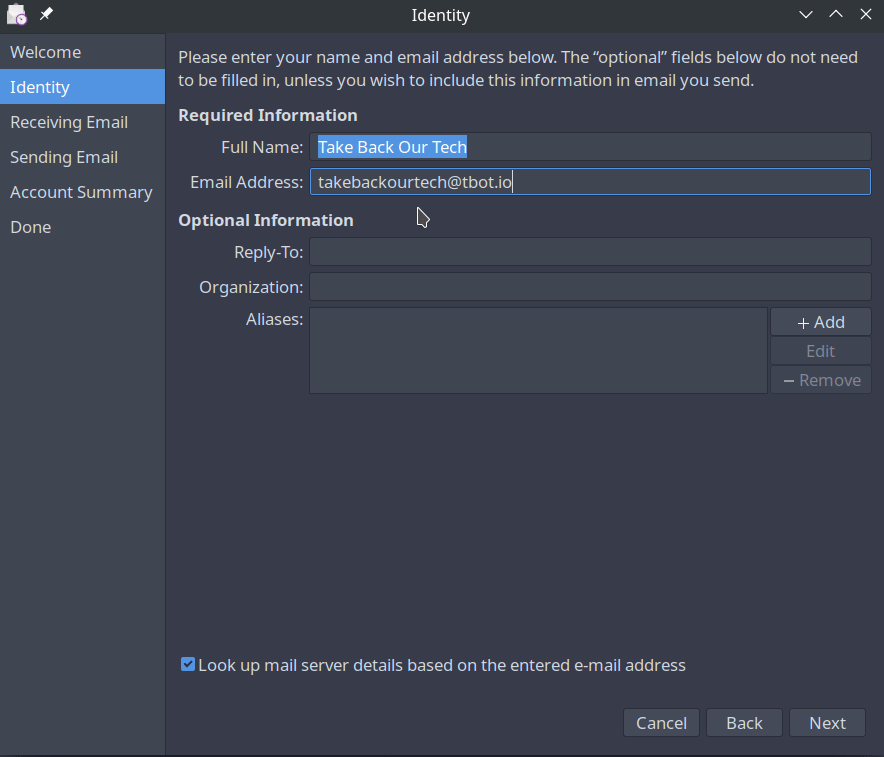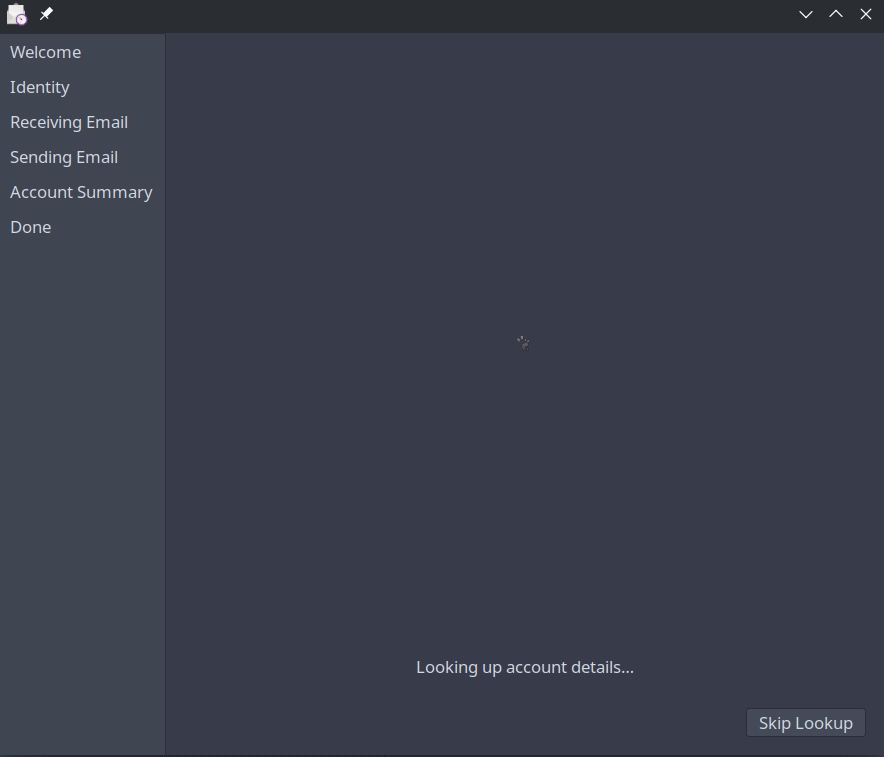
Identity
On this page you need to fill out your Full Name (can be whatever you'd like) and your email address. You will see a checkbox at the bottom of the screen, and can use this to automatically look up email details, however this may not work 100% of the time. If it succeeds, you are done with the configuration and can skip to the end of this section.
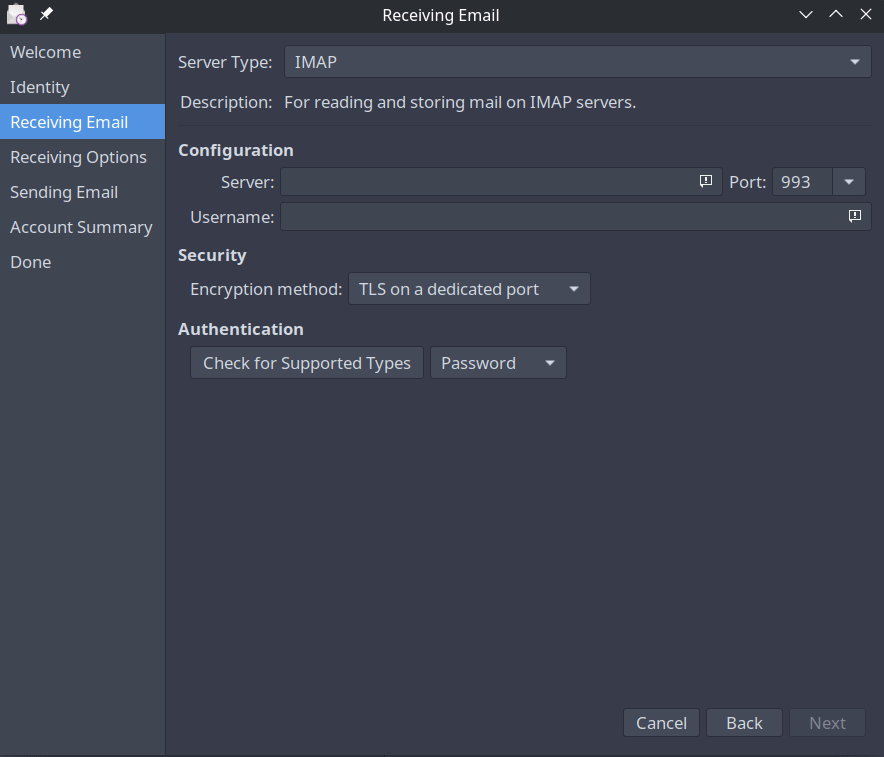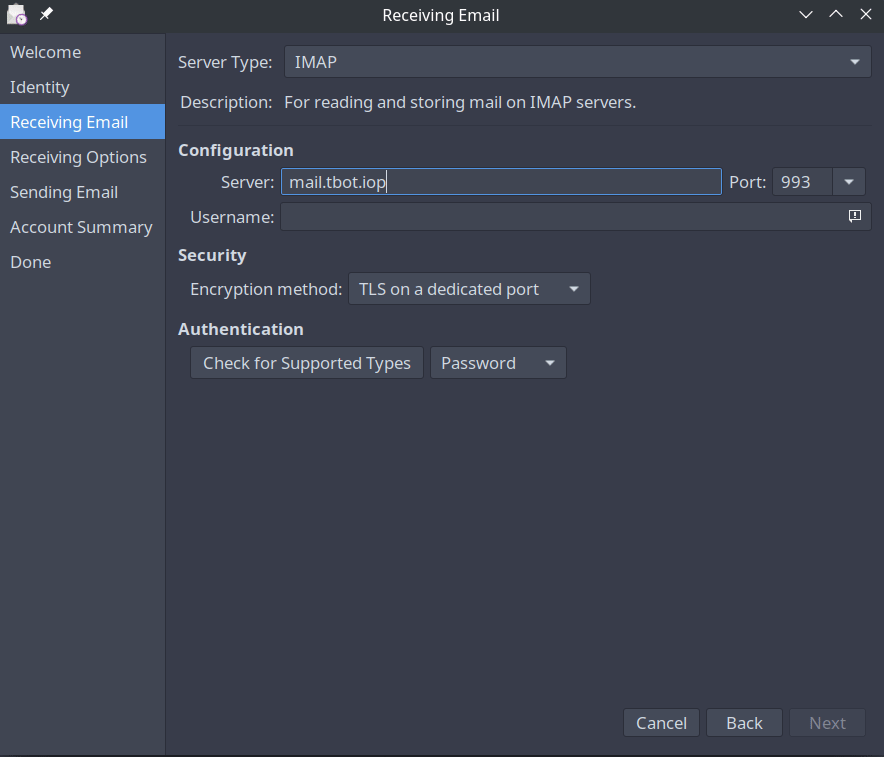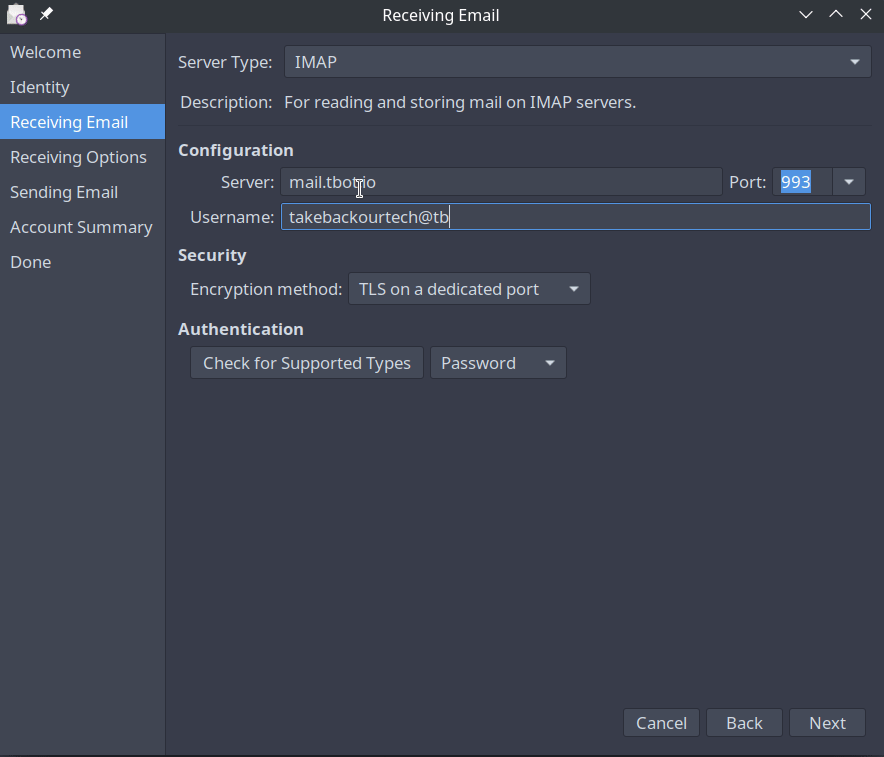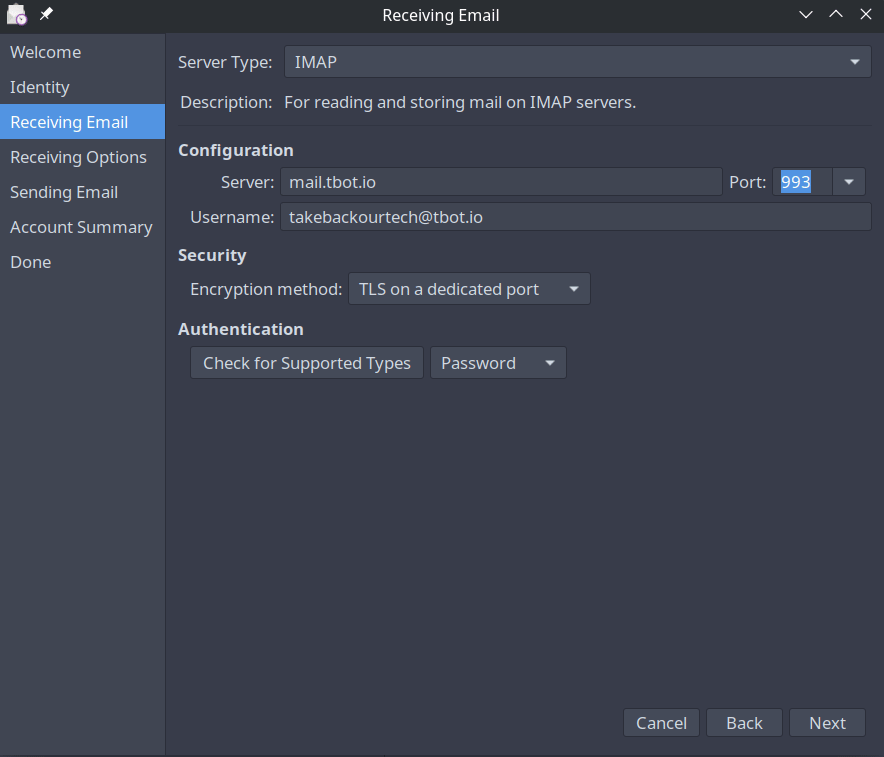
Receiving Mail
On the receiving email page, you will enter your IMAP server address and the IMAP port. Your username will usually be your full email address and should be specified in your IMAP config.
Receiving Mail Options
In the receiving mail options, set checking for new messages to a reasonable time, so you get messages quickly.
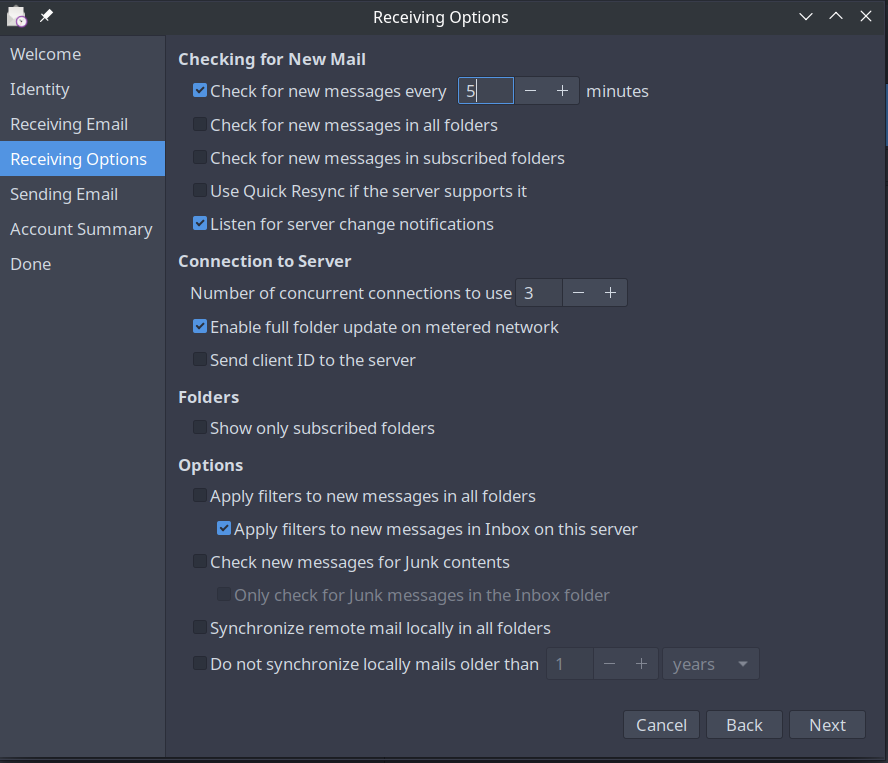
Sending Mail
On the sending mail screen you'll need to enter your SMTP server, this will usually be the same as the IMAP server, but refer to your configuration details. You will need to require authentication, so make sure the checkbox is set. The default settings should work fine.
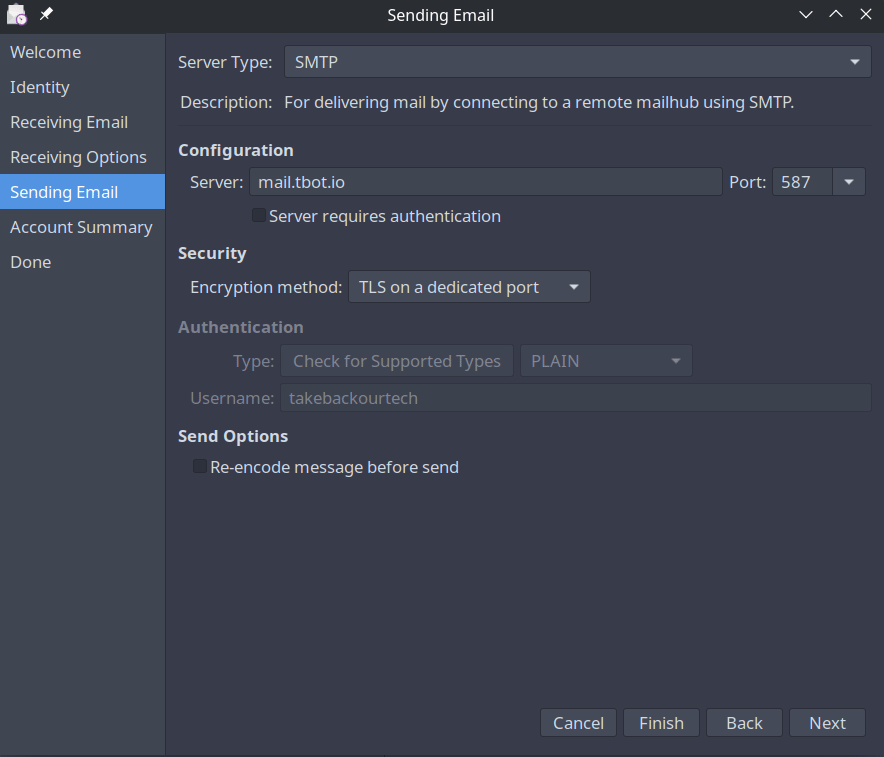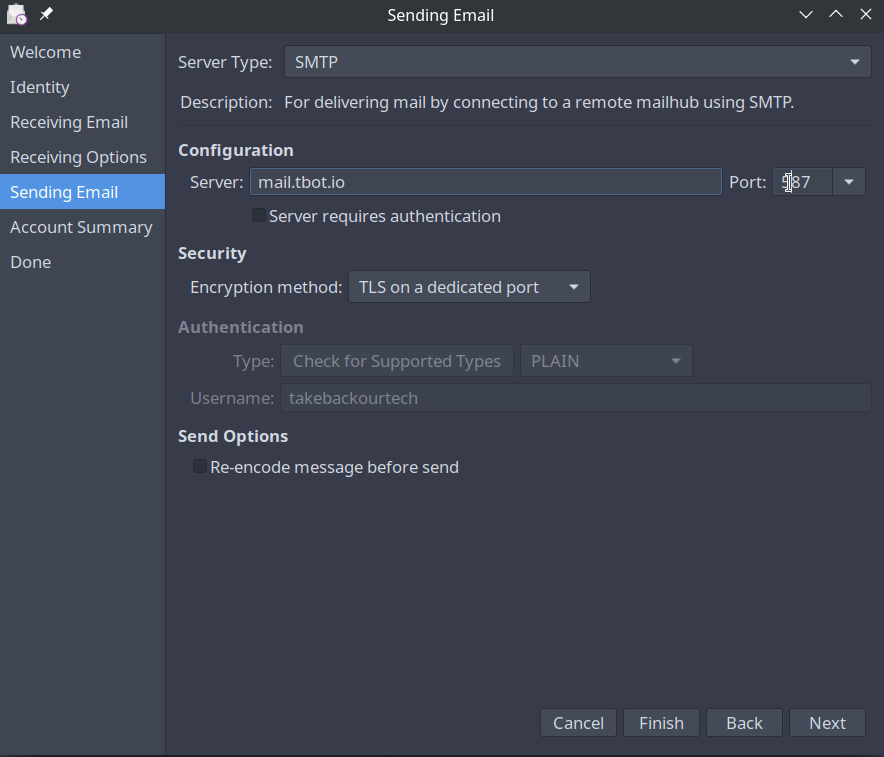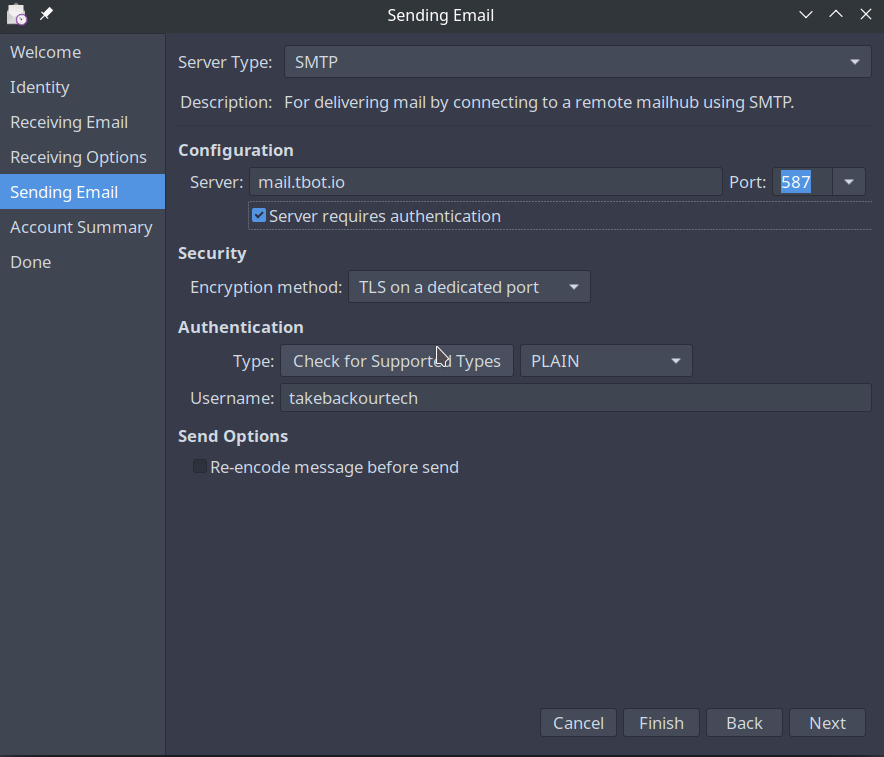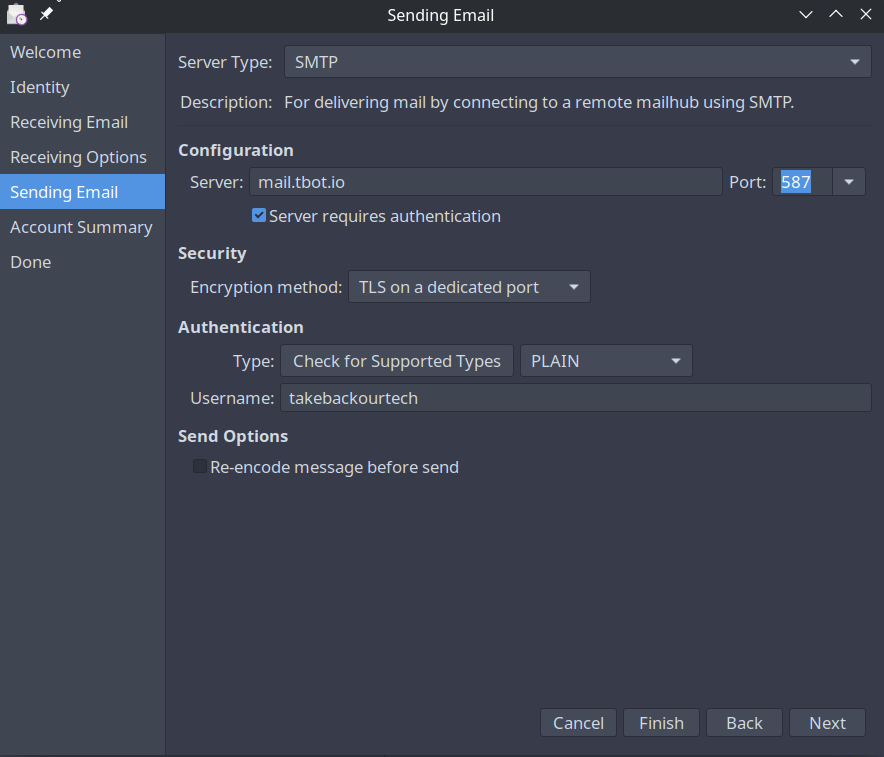
Account Summary
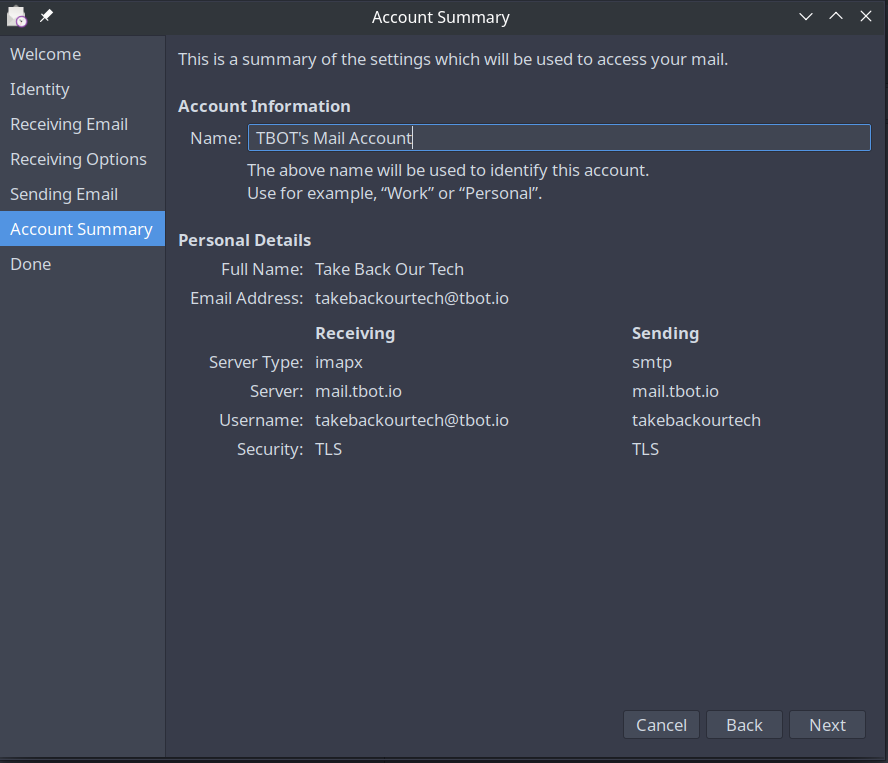
On the last step we will use a name to identify the mail account locally.
Finish Setup
Once you're finished with the setup, apply your settings. If your configuration is correct then Evolution should prompt you to authenticate the account using your email account's password.
If the account continues to load or throws an error, you need to adjust its configuration. Right click and edit its properties. Contact us on the Take Back Our Tech group if you need help.
This process is similar across all mail clients.
K9 Mail Setup
Now we'll walk through the K9 Mail setup which will be very similar, here's the walk through. If you're opening up the app for the first time, you will be guided to Setup a New Account.
If you have existing mail accounts you need to go into your Settings > Manage Accounts > Add New Account.
The first step to setup a new account is to enter your mail account username/password. You will select the IMAP type account, and then enter your configuration
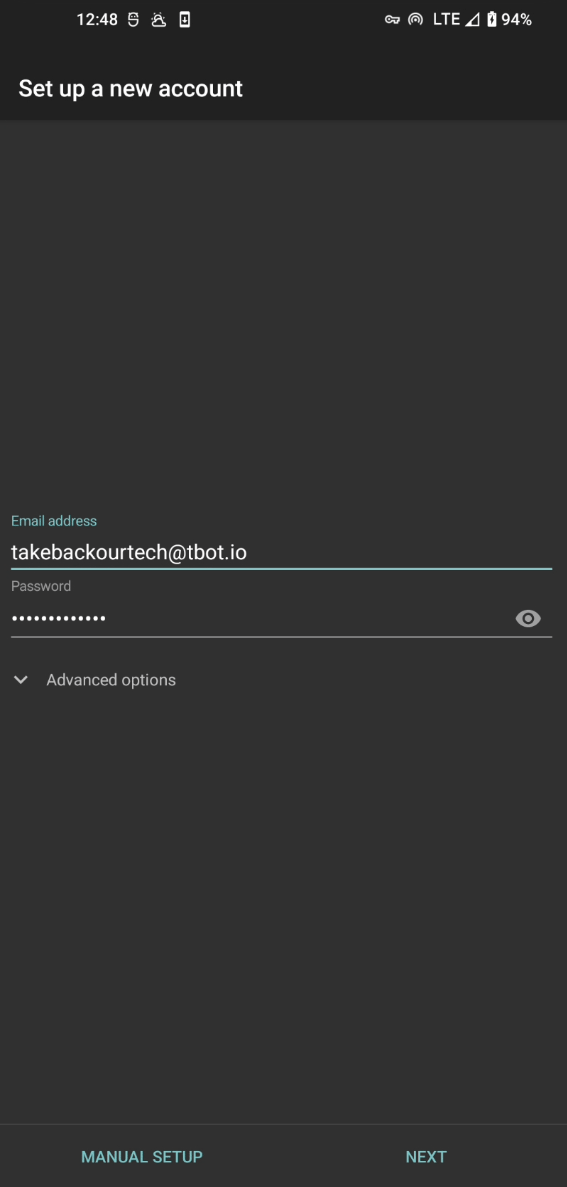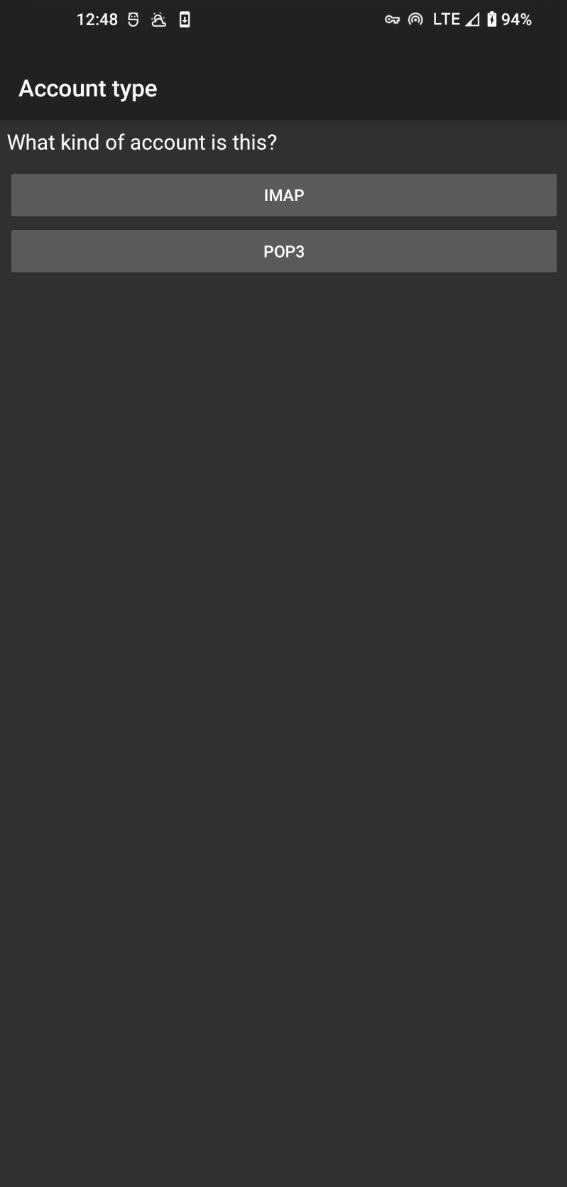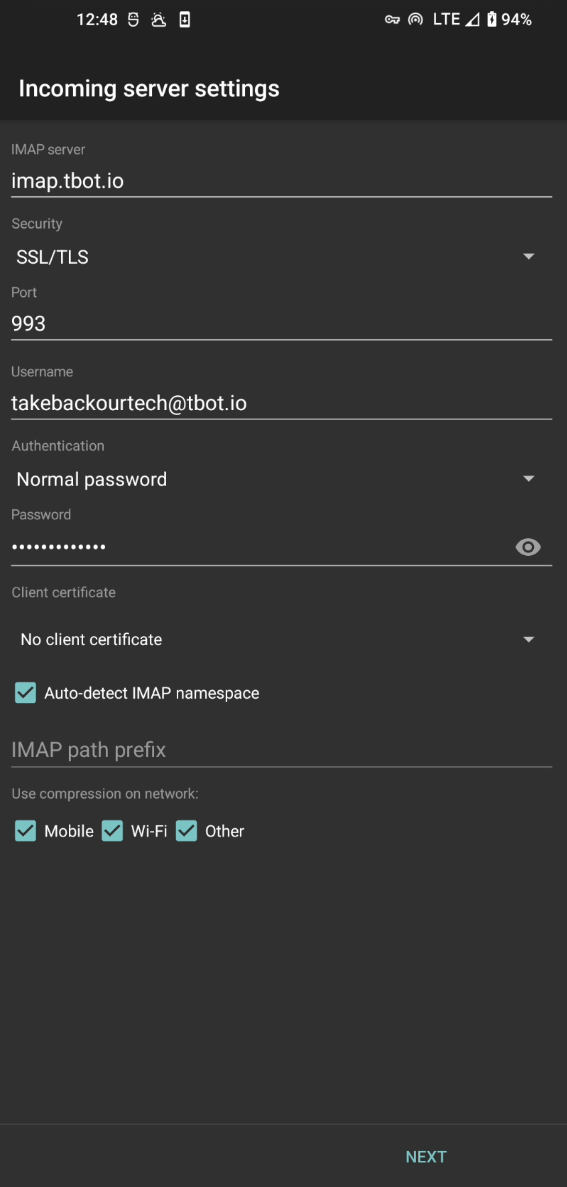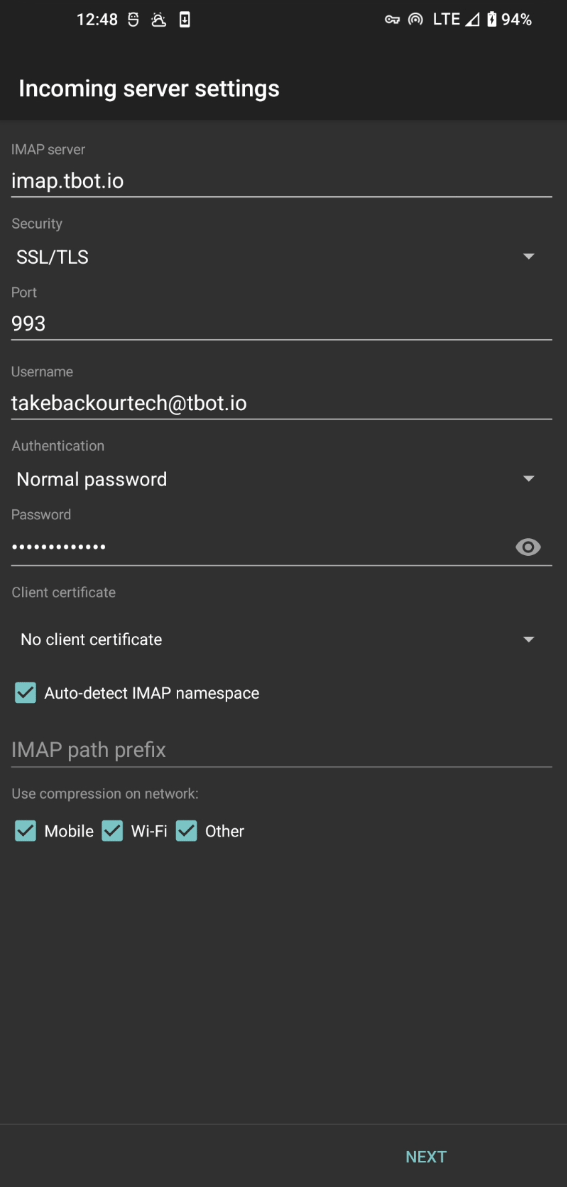
The configuration pages are almost the exact same as the previous configuration setup, so make the same changes again, refer to your IMAP provider's configuration, and let us know if you need any help on the #TBOT Chat.
Testing Your New Emails
Before you continue, just make sure you can send and receive emails! You can test by signing up to our official mailing list ;)
Conclusion
Now you know where to get yourself an email account that is detached from any one single website or application. The next parts will show you how to setup your OpenPGP key so you can end to end encrypt your emails!
Take Back Our Tech Newsletter
Join the newsletter to receive the latest updates in your inbox.





