Who Can We Call On? How Our Phones Are Tracked By Big Tech, Telecom, and Government
Watch The Video
Document Dump:
Here are all the primary sources used in this for this article, feel free to perform your own analysis and share with us.
Password: takebackourtech
Download From Disroot
Buy The Above Phone
ORIGINAL ARTICLE
Introduction
Our mobile phones are the single most important communication device we have. Their function is built ontop of billions of dollars of hardware, software, research, and infrastructure. This results in the fastest, most impressive digital experience the world has ever known. Is this all for our benefit? Do we know the full price we pay?
We may have a gut feeling that data collection exists, yet can't point exactly to what it is. This series is designed to give people a comprehensive overview of how data collection occurs at every layer of the mobile ecosystem by pointing to real world studies and investigative research.
What you will find is haunting. There are highly coordinated efforts between tech and telecom corporations, along with government agencies collectively performing massive dragnet and targeted surveillance of every citizen. This is one of the biggest threats, if not the biggest threat we face today as individuals, families, and communities who value their privacy and freedom.
This article is not meant to incite fear, but we cannot understand the solutions without knowing the problems. We must start with the most observable threats to our mobile privacy. By understanding how the tracking works, the solutions are immediately obvious. You will intuitvely figure out the solutions before the end of this article; before they even present themselves.
Who can we call on? There's only one person that I have in mind. You!
It is important to mention that this is not an exhaustive list of the ways mobile data collection occurs. There are plenty more avenues of attacks that exist. This article simply sticks to the topics that are easily observable through independent study, and can be understood without advanced technical knowledge.
The rest of the series will go into the solutions and how they work in-depth. If you'd rather fix a lot of the issues without knowing why or waiting for the next article (patience is a virtue), I invite you to look into CalyxOS, GrapheneOS, or purchase the Above Phone.
The Above Phone is brought to you by the company behind #TakeBackOurTech, Above Agency. We have put together a privacy phone solution for those who want to tackle the issues listed in this article head on, without having to do a lot of the self-study and setup that is required.
This series will also show you how to do it yourself, we will show you how to install CalyxOS and GrapheneOS on your devices later on in this series.
Let's get into why you need solutions...
The Operating System
There are two main operating systems in use today: Apple's iOS and Google's Android which make up 99%+ of the global market share of mobile OS. With 313.2M shipped in the last year, the data pipeline to these two companies continues to grow at an enormous rate.
Given that large parts of the operating systems are proprietary, it takes well-designed independent research efforts to measure how much data collection has happened behind the scenes. One such study was published earlier this year; Mobile Handset Privacy: Measuring The Data iOS and Android Send To Apple And Google, from the School of Computer Science at Trinity College in Dublin Ireland.
Study Synopsis
This study measured the different data captured by Android and iOS based phones, after the user had opted out of all data collection options.
The study found that large amounts of data were sent back to Google and Apple, on average every 4 and a half minutes. When the phones aren't being used, it was observed that the iPhone sends 52KB every 12 hours, not even close to the 1MB of data Google sends in the same time. Just in the United States, with 113M iPhone users and 129M Android users we can estimate that Apple collects 11.6GBs every 12 hours, while Google collects 1 TB.
To emphasize, this happens no matter what privacy options the user chooses when setting up the phone.
This means, that when you use these operating systems - you are being robbed of your data. You have no choice in being made a victim of surveillance by Google and Apple.
This study was performed using the following steps (summarized):
- Start the handset up following a factory reset
- Remove and re-insert the SIM card
- Leave the handset idle for a few days
- Login to an app store
- Open the 'settings' app and toggle 'location services'
What information was gathered?
The following section outlines when exactly the unique identifiers are sent off the device. When multiple IDs are sent out, that information is easily connected to each other, creating an association graph.
Apple / iOS Data Collection
Apple can use the following information to single out a device, network, or cellular plan. It is concerning that the MAC addresses of devices on your your local network are sent with geolocation when possible.
On Every Single Connection:
- IP Address Of Phone: An inherent part of every single network connection made to a back-end server, and can be used to estimate location. Your IP will change dynamically if connecting to cell towers, allowing for the analysis of movement.
On First Start (restarting the phone from a factory reset):
- UDID: Unique device identifier, unique to the physical device.
- Hardware Serial Number: Another code that uniquely identifies the device.
- Unique Chip ID: Unique to every System-On-A-Chip (SOC). This is the chip that integrates your CPU, storage, modems, and other phone components
When a SIM Card Is Inserted:
- IMEI: (International Mobile Equipment Identity) that uniquely identifies your device across GSM networks
- Phone Number: Phone number with area code.
- IMSI: SIM Serial Number
Reglularly When The Phone Is Idle, Observed Every 2 to 3 Days:
- Local Device MAC Addresses & GPS Location: The MAC addresses (local network identifiers) of all devices connected to the same WiFi network along with GPS location if Geolocation is turned on.
- UDID
- Hardware Serial Number
- Apple Advertising ID
- IMEI
- Phone Number
- IMSI
When Interacting With Settings
- Hardware Serial Number
When Turning Location On
- All local MAC addresses along with GPS geolocation.
Google sends all the exact information as Apple, with the absence of location - however that can be easily gathered through the use of Google Maps, and connected by your Android ID. Especially concerning with Google is the IDs sent every 10 to 20 minutes which show an interest in phones that change numbers or cellular service.
On Every Single Connection:
- IP Address Of Phone: An inherent part of every single network connection made to a back-end server, and can be used to estimate location. Your IP will change dynamically if connecting to cell towers, allowing for the analysis of movement.
On First Start:
- RDID: Resettable Device Identifier or Ad ID, used for Google Ad Services, sent on startup, and regularly sent to Google's attestation service
- Hardware Serial Number
- Android ID
- WiFi MAC Address: The MAC address of your local network's router. (not all the devices)
- IMEI
Inserting a SIM Card:
- Hardware Serial Number
- Android ID
- IMEI
- IMSI
- Mobile Carrier Information
- Phone Number
Sent Regularly, Observed Every 10 to 20 Minutes
- Hardware Serial Number
- Mobile Carrier Information
- Phone Number
Sent Regularly, Observed Every 2 to 3 Days
- Wifi MAC Address
- IMEI
- IMSI
- User Email Address
Special Characteristics of Data Collection
There are a special aspects to this data collection that go above-and-beyond the data collection one would normally expect for the support and service of a device.
Time Tracking: Connections back to Apple servers averaged once every 264 seconds, while connections to Google servers averaged once every 255 seconds.
No Way Out Of Telemetry: No matter what settings a user chooses or whether an Apple / Google account is currently active, logs from multiple sources are aggregated and sent back. In Google's case, the following device services are observed as sources sent in batches to the Google Play Services logging endpoint. These logs account for how much larger Google's data stream is than Apple's.

Additional Apps & Services Collect Data: Existing apps integrated into the operating system also are used to gather data. For Apple, the ITunes, Siri, and Safari services were shown to phone home. For Google pre-installed system apps like Nexus, Clock, SafetyHub, Firebase, Youtube, Chrome Browser, Google Docs, all make connections to Google servers.
Geolocation Tracking: Unique to Apple we find that when location is enabled not only is the current device's MAC address (which identifies the device on a local network) sent out, but also ALL the devices on the local WiFi network along with the geolocation coordinates accurate to within 10 meters. This enables Apple to create a device map around any iPhone with or without the consent of other devices on the network.
How can this data be used?
When this data is collected individually, it may seem like meaningless numbers and codes are being recorded. However, when put into the larger picture of regular device-level activity-logging, a comprehensive constructed identity emerges for each graphed device.
Information Graph
Each one of these pieces of information can easily be connected to a body of data that represents one identity. When multiple device identifiers are sent in one request those data points are confirmed associations. This was observed at every stage in the study experiment. As time goes on, additional data points are added on to the body of information, associated by any of the previous identifiers collected. Any new phone numbers or cellular subscriber information is easily captured, creating a set of phone numbers connted to identity. Web traffic through the built-in browsers as well as telemetry and data collection from third party apps are easily associated through use of the AndroidID and Apple Advertising ID that occurs when downloading the application.
Personally Identifiable Information
Since Google and Apple also provide web browsers and payment services on these devices, it is natural that any telemetry transmitted from these sources will be added on to the body of information. Since Google Pay and Apple Pay collect credit card information or email accounts to access their application stores, the real identity of users and the association to their phone is fully guaranteed.
Location Tracking
The continuous requests (on average every 5 minutes) back to Google and Apple servers sends your device's current IP (Internet Protocol). This IP can be used to infer general location since most cellular providers update the IP address based on where you are in the world. If you are on the move, then every subsequent request would reflect a change in location, creating a real-time graph of where you've been. In special cases such as Apple's geolocation telemetry, Apple collects all the MAC addresses of devices connected to the same network as the phone. This allows it to build a location map of potentially every device in the world that can be cross-referenced in the future by other means.
Tee the robot wants you to follow us on these alternative social platforms:
Official #TakeBackOurTech Community
Telegram Channel
Telegram Discussion
Odysee
Hive
Minds
The Apps
Every mobile platform has its own ecosystem of apps developed by independent third party developers. The two most popular app stores in use today are the Google Play Store and the Apple App Store. Although it is expected that apps will communicate and send data back to the application developer's servers, there is also a hidden layer of software dependencies that developers use - in the form of third party services.
Our next study will look at these third party services installed in common mobile apps, their roles as Advertising & Tracking Services, what information they send to third parties, and the companies behind it all.
Consideration
The following study took place before Android 10 was released in September of 2019, which changed the permissions for device identifiers to make it harder for apps to access them. After this update, only official Google apps or privleged system apps would be able to access the data. The following device identifiers became protected:
- IMEI (GSM) or MEID (ESN/CDMA)
- SIM Serial Number (ICCID)
- IMSI (Subscriber ID)
- Hardware Serial Number
Also in Android 10, devices started reporting a randomized MAC address to third party applications. Although this was a huge improvement for Android's privacy, tremendous damage was already done. Third party applications can still access the phone number and AndroidID to continue tracking behavior, and as we'll see now - years of gathering unique device IDs along with supplmentary data such as email and phone number enable only the advertising and tracking companies and their parent companies to continue cross-referencing new data, even if the collection of new unique device identifiers is disallowed. We also have to remember that Google & Apple's own collection of genuine device identifiers has not been curtailed and continues to be observed on a wide-scale in 2021.
Study: Apps, Trackers, Privacy, and Regulators A Global Study of the Mobile Tracking Ecosystem
Study Synopsis
This study was performed in several parts that built of each other:
- Crowdsourced 12,000+ study participants with Android phones that allowed researchers to observe their phone's outgoing traffic to different domains.
- Retroactively analyzed the traffic to discover what third party Advertising and Tracking Services (ATS) were in use, and further classifying them.
- Identified the companies behind the ATS services, and traced their parent companies to understand the data sharing policies.
What information was gathered?
By intercepting the network traffic of 11,000 Android users using Lumen Privacy Monitor, the researchers were able to monitor unique identifiers (UIDs) that were shared with third party domains. It is important to note that these were not first party domains, or domains core for the usage of the apps, but separate third parties that were collecting information directly off the phone.
The following list of identifiers were observed to be sent to these third-party domains:
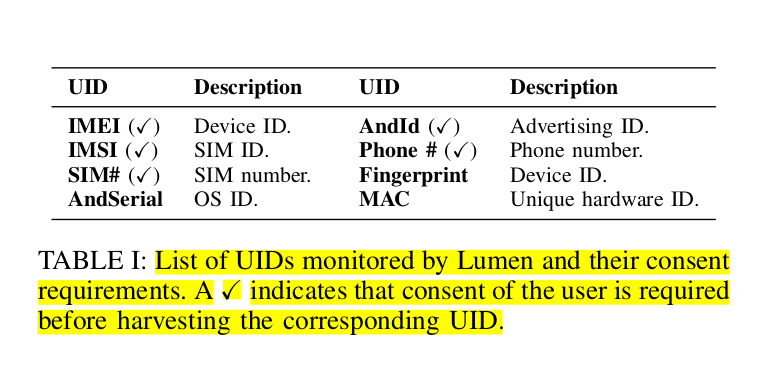
You will immediately notice some of the familiar identifiers already shared with Apple and Google in the first section. Many of these can uniquely identify the device and person immediately with access to the right datasets.
What apps were sharing data?
Although no specific apps are named, the study monitored 14,599 different applications on and off the Google Play Store in 33 different Google Play Categories with around half of the apps having more than 1 million installs. In other words, the data collection observations in this study would be typical of an average mobile user.
What kind of domains were the UIDs being sent to?
The study breaks down the different server names (domains) being sent UIDs into third parties, UID harvesting third parties, ATS, and ATS-C.
Third Parties: Any domain not connected to the developers of the application.
UID Harvesting Third Parties: Any third party that was observed gathering UIDs.
ATS (Advertising and Tracking Systems): A third party that was labelled as a ATS domain through a classification model trained on normal and tracking domains. Domains in this category were 'doing their job' openly, collecting user data for the purposes of advertising, tracking, and analytics.
ATS-C (Advertising and Tracking Capable): These were domains not classified as Advertising and Tracking systems though they harvested UIDs. These domains are 'unofficial' trackers which for all functional purposes identifiers track but cannot be tied to a company or organization that performs tracking services. It is a mystery why they gather this data.
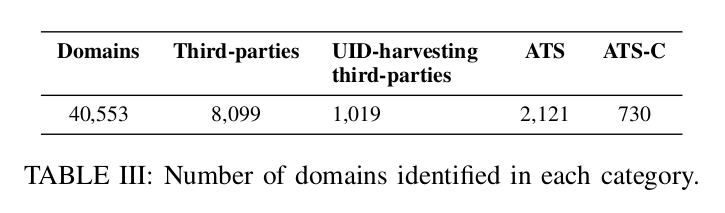
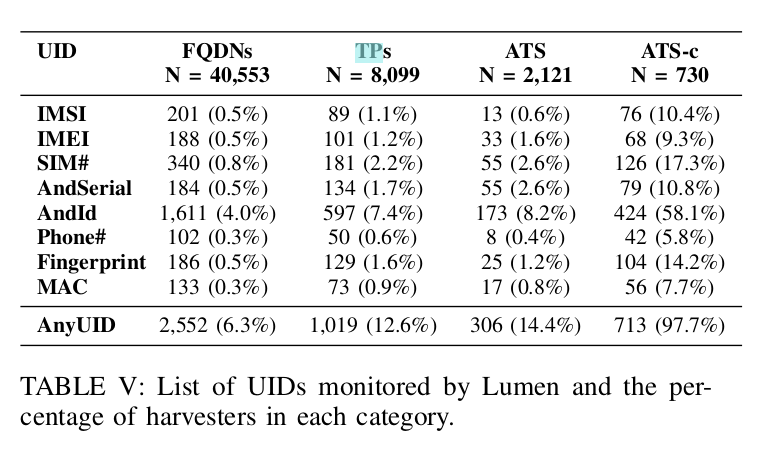
In the figure above of domains that harvested UIDs, we see some troubling signs:
- Only 14.4% of ATSs harvest UIDs (suggesting other techniques are in use like HTTP headers, cookies, tracking pixels)
- UID collection percentage was highest among ATS-C, which means that there is a lot of UID collection going towards unknown sources
- The IMEI (the same ID shared with the operating system and cellular service providers) is regularly collected by ATS and aTS-C domains
- The Android ID is heavily collected by all domains, which suggests that the ATS / ATS-c domains can track analytics for one Android user across multiple applications
What parent companies are behind the tracking?
The study then attempts to look at the organizations that own these domains. Subsidiaries of an organization share data with each other, so one must look at not just the Analytic or Tracking company but the parent company that owns it.
The study made the following observations:
- 16 out of the 20 most pervasive ATS and ATS-C domains are owned by Google's parent company Alphabet
- 292 parent organizations own 2,000 ATS and ATC-C domains
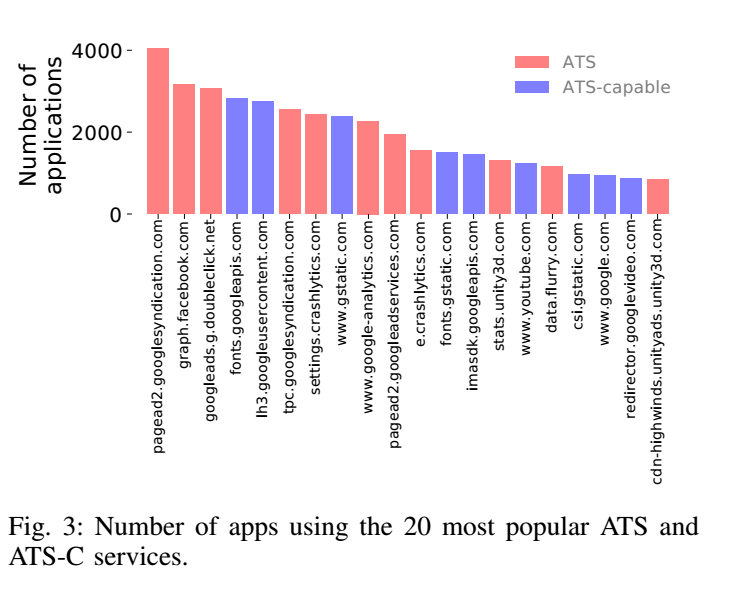
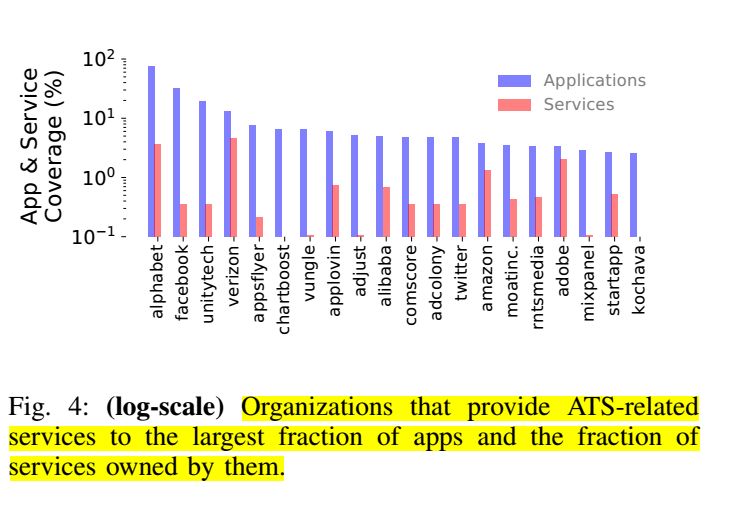
The major concern here is that the Alphabet, the parent organization of Google has access to the operating system level collection of UIDs, and additional detailed tracking information through its subordinate ATS and ATS-C (ATS Capable) platforms. This gives Alphabet an incredibly in-depth look, reach and access into at your phone's activity within the operating system, and within apps themselves.
Additional Concerns
Multiple ATS's In Use
Many applications use multiple advertising and tracking services within an app. The average mobile app connects to 11 different domains, 4 are ATS-C domains. 82% of apps connect to at least one ATS system, and 75% of apps connect to at least one ATS-C system. 29% of apps connect to at least 5 ATS domains, and 29% connect to at least 5 ATS-C domains.
Cross Device (web) Tracking
These ATS domains were analyzed to see whether the company also performs web based tracking. This would allow them to surveil users across devices. The study looked at all the web tracking domains embedded the Alexa Top 1,000 sites using virtual machines. 39% of ATS's are present online, and many are very pervasive in the web ecosystem. Meaning if you visit enough sites on your computer and use apps on your phone, it is trivial for a cross device ATS tracking company to connect the usage.
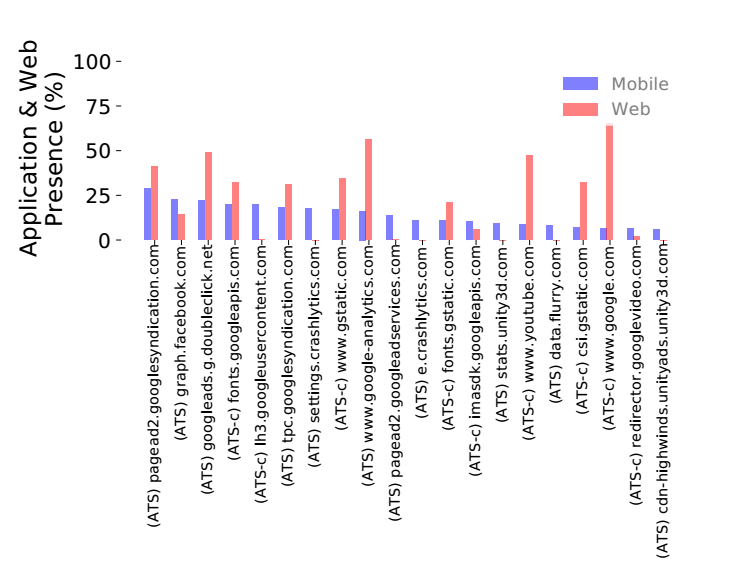
Subsidiary Sharing
Looking at the privacy policies of the top 10 ATS parent organizations shows a data sharing agreement between them and their subsidiaries. Many of these companies reserve the right to share ATS-related data with third-party partners - meaning that your data is shared with any organization with whom they decide to partner with. Since the parent companies are tech and telecom giants including Google, Facebook, and Verizon, these ATS's have filled many of the missing links between the usage of mobile apps, the operating system, web, and cellular systems.
Conclusion
The last section should have made the state of things clearly apparent. Not only are our phones tracked at the operating system level by Google & Apple, but by simply using an average app, we subject ourselves to even more data collection at the hands of advertising and analytics companies. The data collected can vary, but usually will be filled with tracking and detailed usage data easily associated to your phone and identity using the unique identifiersAndroidID. And it all trickles downstream into the ocean of data in Google and Apple's hands. Although we didn't look at Apple's iOS in this particular study, there have been previous studies tracking information shared with third parties on iOS apps. In this study, Apple (the domain apple.com) was listed as receiving sensitive data from 17% of applications, third on the list behind 2 Google domains.
The Cellular Service Providers

Before our phones did everything except toast bread, we just used them to call and text people. Today, cellular service providers play an integral part in modern communications handling our calls, texts, and data. But one question remains, should we trust them? All signs point to hell no.
How It Works
Most modern cell service today occurs on LTE (Long Term Evolution); the 4th generation of wireless communication started in 2010. We won't go too deep into the technicalities, but LTE isn't a new network, it's an improvement over existing GSM and CDMA protocols that allow for higher data transfer speeds. A requirement of LTE is that communications happen over the internet.
Most of us today use GSM (Global System for Mobile Communications). GSM allows us to carry our cell service information on SIM (Subscriber Identity Module) cards. We can swap this into any GSM enabled phone, and customers are identified by SIM identifiers. CDMA phones do not need SIM cards, customer are identified by device identifiers on CDMA whitelists.
When we activate and use our phones, they communicate unique identifiers to the cellular networks that allow the networks to identify us as customers, and to connect us together.
The IMEI (International Mobile Station Equipment Identity) we observed being sent to Google and Apple in the first section, also was sent to the app trackers in the second section. This is very concerning because IMEI can be used to uniquely identify your device. It is generated by the manufacturer and registered by your network. It can be used to recognize stolen phones and ban them from the network.
The IMSI (International Mobile Subscriber Identity) is an identifier that exists on your SIM card which identifies the country, location, and subscriber number in the home network.
When we make calls, send texts, or generate internet traffic on our phones - these identifiers are attached to them directly or indirectly. As we'll see, cellular service providers hang onto this data for a long time.
What cellular data is saved, and for how long?
Although this information is never shared openly with the public most cell phone companies store customer data for a very long time. In 2011, an ACLU coordinated records request on cell phone tracking uncovered a Department of Justice document which outlined the data retention policies for the top five cell phone providers. This document was intended to assist law enforcement with obtaining cell phone records.
Keep in mind that the following information definitely has changed, but will give you an idea of real data retention as the public rarely gets to see it. Analysis of this document is as follows:
- Your call detail records are held on average for 2 years up to 7 years (AT&T) or indefinitely.
- Your cell phone tower usage (an easy way to determine general location) is kept from a year up to indefinitely (AT&T)
- Your text message metadata can be kept from a year to 7 years (AT&T)
- IP sessions can be kept up to one rolling year, with internet traffic held up to 90 days
More recent information on retention periods came from an independent forensic consultant in 2015 who reached out to telecom companies individually. His findings indicated that certain retention periods such as those for phone calls had been extended.
It is amazing how little current information can be found concerning retention periods, and the lack of transparency is almost always a bad sign.
The major point here is that your cellular usage can be used against you, and for a long period of time. Although the content of your calls and texts aren't saved (as far as we know), the metadata tying you to your contacts is available for search and subpoena from law enforcement. Call details aren't just phone numbers and durations, they also include the cell towers used in the call which can used to determine location and movement.
So how is this information actually collected for use against individuals?
Cellular Warrants
As the aformentioned ACLU records request show, our cellular providers act as data brokers to law enforcement agencies. In order to keep up with subpoenas and warrants, telecom started charging for records requests.
The following documents outline telecommunications support for law enforcement, and give us an idea at what services were available at that time. They include guides to subpoena information from the likes of AT&T, Comcast, Sprint, Cricket, Nextel, and Verizon.
These documents suggest that police officers faxed and mailed in their warrants and supporting documents requesting access to call & text records. Check out pages from the guide to the Verizon Wireless Law Enforcement Resource Team.

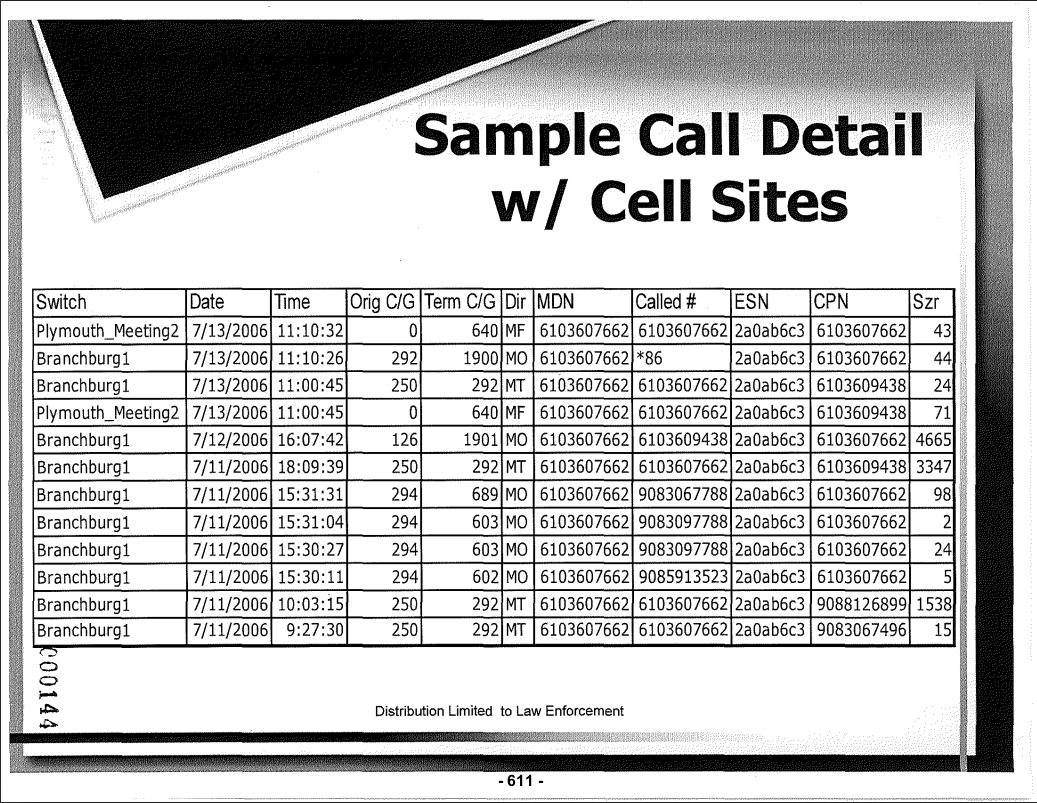
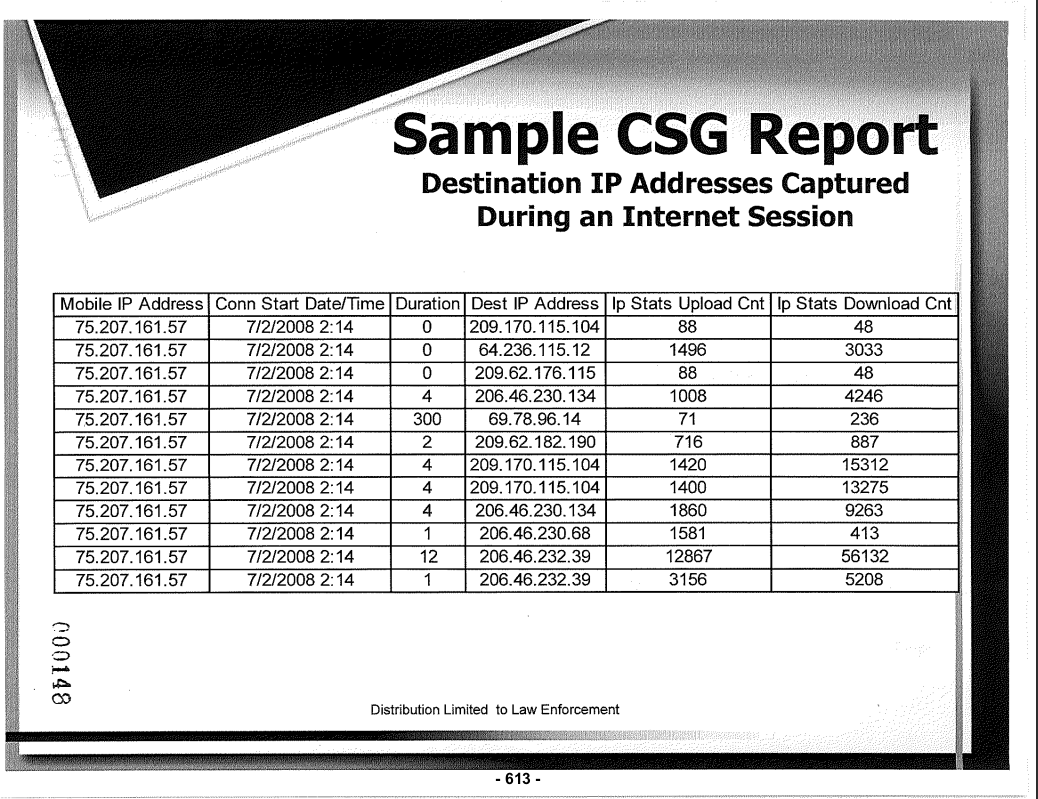
These manuals guide law enforcement on what data can be requested, which includes call/text/internet records, location tracking, and customer information. It also shows how wiretaps and pen registers (active monitoring of all calls/texts/traffic) can be initiated for a customer.
Geofence Warrants
At the end of 2020, Google released information on the rise of Geofence Warrants it was receiving from Law Enforcement, seeing a dramatic surge from less than 500 every quarter in 2018 to 3000 at the end of 2020.
What are Geofence Warrants?
These are search warrants that 'compel' Google to disclose the users that were in the vicinity of a given place at a given time. How does Google have this information?
If you use an Android phone and have your location history on, your location data is collected in an internal Google database called Sensorvault.
The story was first broken by the New York Times, reporting how popular these warrants had become with local law enforcement. Agencies would use the Sensorvault database to obtain warrants, requesting information on an area and a period of time. Google would then respond with the location information on all devices in that area. When Congress became aware of the existence of Sensorvault, they had questions of their own.
Although the extent of Sensorvault's tracking, data retention, and sharing remains a secret - the impact on those caught in the dragnet has never been clearer.
Jorge Molina was arrested for murder after his phone turned up in a mass geofence warrant. "As a result, Molina dropped out of school, lost his job, car, and reputation, and still has nightmares about sitting alone in his jail cell." Jorge was innocent.
Sensorvault is a perfect example of the modern surveillance state we live in. Its database could be used to track any Google user, wherever they are at any time. Its use in Geofence Warrants is dangerous territory that we continue to march towards.
Google is not alone in its geofence capabilities, Apple, Lyft, Snapchat, and Uber all receive these warrants but have not indicated their level of cooperation.
When Warrants Aren't Needed
In the last two cases, the telecommunication providers and Google required a court-ordered subpoena or search warrant to begin processing the information. However there are programs that do not require a ruling from a judge and can be internally approved through 'administrative warrants'. These programs are run by the alphabet agencies and strategically hidden from the public.
One major program that was revealed to the public is DEA's Hemisphere.
Hemisphere
Hemisphere emerged in 2007 and was funded by the White House's Office of National Drug Control Policy and the Drug Enforcement Agency. Its goal was to provide federal and local agencies near real-time search capabilities across billions of call detail records (CDRs). The program partnered with AT&T to collect CDRs across any telecom provider that used an AT&T switch. Through this program, 4 billion new call records were collected every day - and CDR data going back to 1987 was also integrated its database.

Results of EFF's FOIA and Lawsuit Against the DEA
A major overstep of this program was the way it used administrative subpoenas, which could be issued by any law enforcement agencies and approved without a court-order. Officers that used the program could request call detail records & analysis on any group of numbers.
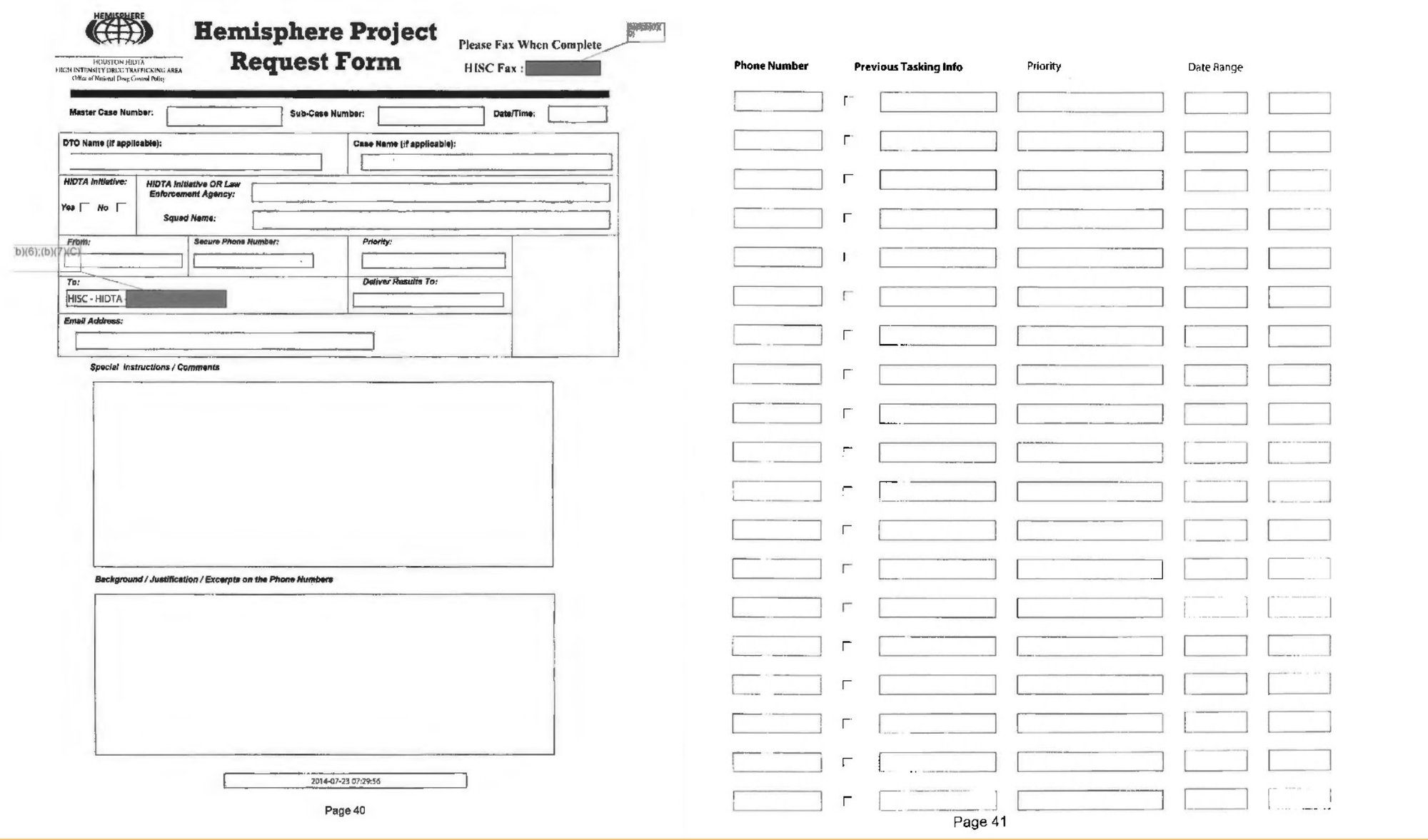
These administrative subpoenas are submitted to High Intensity Drug Traffic Area Offices (HIDTA), which supervises the requests being processed by Hemisphere analysts. The entire operation can take place in less than an hour.
This project was particularly effective at connecting multiple phone lines with individuals, even if not registered in their name.
- Dropped Phones: An algorithm that is used to find the new number of a person who has gone dark on their existing line
- Additional Phones: A program that can be determine whether a target has additional phones
- International Phones: A program that provides records for international or roaming numbers
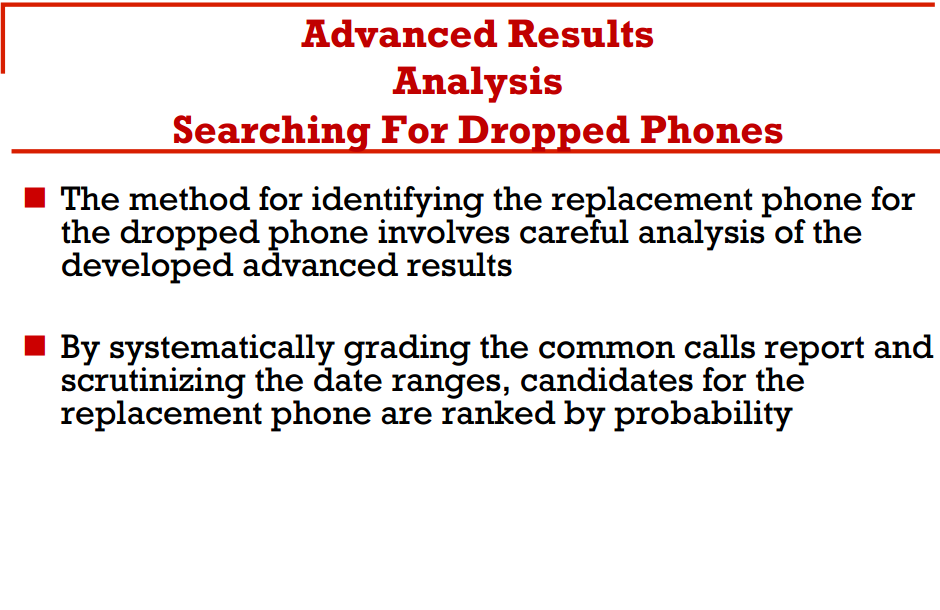
From these slides, we get some idea of the algorithm; and its not rocket science. The algorithm weighs other potential phone lines based on whether:
- It called the same numbers
- What date it became active (dropped and picked up activity)
Since this system has had close to a decade to be improved, we can speculate that location data could be used in today's searches. This is likely because location information was one of the earliest features of this project, and we know tower data is collected by many telecoms, easily integrated into their analysis.
The people involved in Hemisphere took major precautions to hide its existence from the public, by not listing it by name in official and internal reports (such as the DEA's common G6 report).
Investigators also hid the use of Hemisphere in their investigations by constructing parallel subpoenas for the actual records as evidence used in the courtroom.

When used in court, defendants could not tell that the evidence was reconstructed rather than deduced. Would you consider this highly illegal? Some might.
Did the program's effect on crime justify its abuse of power?
Conclusion
Hemisphere shows us that deep state surveillance programs can be massive in scale, and completely self-contained. Programs like these go to incredible lengths to hide themselves from the public. They also show a high level of technical sophistication that makes being anonymous very difficult, even with burner phones. Our knowledge of these programs is dated and highly limited. It has been a decade, and their work likely has not stopped. Hemisphere is just one of many Deep State surveillance programs. Other infamous programs include FAIRVIEW, PRISM, and ECHELON. All these revelations make me think twice about using mobile service.
Principles Of Cellular Responsibility
In the face of massive, coordinated opposition, there is one thing we can do: be aware of all the different layers of surveillance. We now have a better picture of how exactly cell tracking works, and with this information we have a natural set of responsibilities as a safe mobile user.
Principles Of Cellular Responsibility
- Be aware of the telecommunications collection process. Consider all phone calls and texts compromised. Operating without a SIM card is safest, using trusted WiFi networks instead. If you use a SIM card, many precautions must be taken to disconnect your usage from your previous identity.
- Take ownership of your phone's operating system. Replace your traditional phone or operating system with an open-source OS (operating system) that removes corporate tracking. Buy an above.phone or install GrapheneOS and CalyxOS on your own phone with the guides that will be released later in this series.
- Adapt to using friendly software services & applications. As we've seen, traditional app developers sell their users data through advertising and analytics services. On de-googled phones, we don't use the traditional play store, but use free and open source apps from sources like F-Droid. Apps here go through a screening process and are more transparent about the services to which they connect. We should avoid logging into our previous big tech accounts on our new phones, at risk of deanonymizing our phone. We should monitor and control our application traffic using our new OS and block apps as necessary.
- Protect your internet traffic and communications. When at all possible, use a VPN service that you trust combined with encrypted communications. The Above Privacy Suite offers both of these services. Instead of making phone calls, try encrypted calling using XMPP.
How many of these points did you see coming? The next article will go in-depth on each of these four principles, and will include a demo of the tools you use to achieve them, and how exactly they will protect you.
Conclusion
There is no one we can call on to ensure our privacy except ourselves. The organizations listed in this article have designed the mobile ecosystem so that it's data feeds into their coffers. It takes a concerted effort and lifestyle change to remove all of the tracking from our devices and internet usage. Not everyone will be willing to go to the trouble, but those who do will be setting themselves up to operate unimpeded far into the future.
Remember, our connection is sacred.
Take Back Our Tech Newsletter
Join the newsletter to receive the latest updates in your inbox.